Public Key & Private Key: A Detailed Guide
The field of cryptography is fundamental to many cryptocurrency systems such as Bitcoin. Cryptography is the practice of secure communication in the presence of third parties. In other words, cryptography allows for data to be stored and communicated in such a way that third parties are prevented from reading the contents of what has been communicated. Cryptography is utilized in the creation of a public keys and private keys to make cryptocurrency systems a secure network upon which users can safely operate.
The concept of ownership in a cryptocurrency system revolves around three interconnected elements:
- Digital keys (Public Key and Private key)
- Cryptocurrency addresses
- Digital signatures.
Among these elements, digital keys hold the utmost significance as they enable the ownership features found in cryptographically secure cryptocurrency systems. It's crucial to understand that these digital keys are not stored within the cryptocurrency networks themselves. Instead, they are created and stored by cryptocurrency wallets, which exist independently of the network.
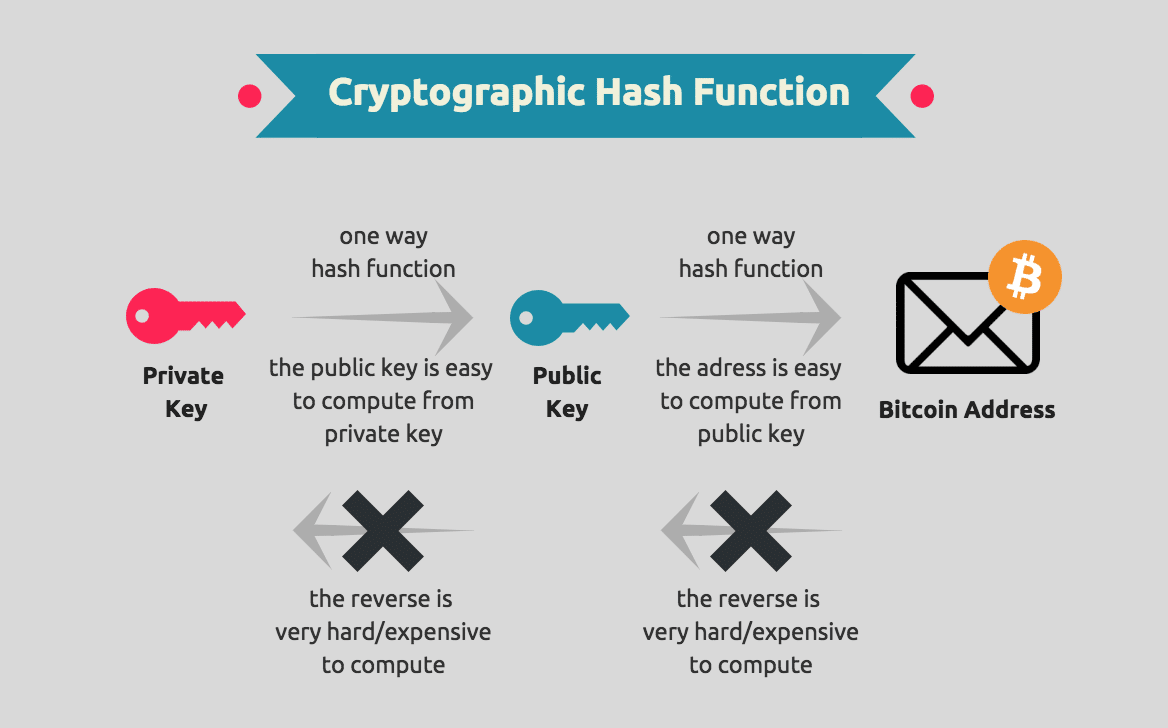
Digital keys are generated in pairs, comprising a public key and a private key. The public key serves as an individual's bank account, while the private key functions as the secret PIN to access that bank account.
The public key and cryptocurrency address are closely linked in a cryptographic manner. The cryptocurrency address is derived from the public key and acts as a representation of it. Typically, the public key is utilized to generate the actual cryptocurrency address. This address functions as a unique identifier for a user's account, enabling funds to be received and deposited into it.
Public Key
The important aspect to understand about the incorporation of public key cryptography in cryptocurrency systems such as Bitcoin, is that they are practically irreversible. This means that the mathematical functions that constitute public key cryptography are relatively easy to calculate in one direction, and are practically impossible to calculate in the opposite direction. This cryptographic feature is at the heart of cryptocurrency systems, because it facilitates the creation of digital secrets and unforgeable digital signatures that are essential for ownership on these decentralized networks.
Cryptocurrencies such as Bitcoin utilize elliptic curve multiplication as the foundation for their cryptography. Elliptic curve point multiplication is the operation of successively adding a point along an elliptic curve to itself repeatedly. It is used in elliptic curve cryptography as a means of producing a one-way function, which is a function that is easy to compute in one direction, but difficult to do so in the opposite direction. In cryptocurrency systems such as Bitcoin, this one-way function takes the private key as an input to generate the public key, which is the output.
Because of this, owners of a private key can confidently distribute their public key with the knowledge that no one will be able to reverse the function, and calculate the private key from the public key.
Cryptocurrency Addresses
A cryptocurrency address is simply a string of alphanumerical characters that a user can share with anyone that wants to send them money. As mentioned before, a cryptocurrency address is effectively a representation of the public key. An address is derived from the public key through the use of a one-way cryptographic hash function. With Bitcoin, the algorithms that are used to make a bitcoin address from the public key are the Secure Hash Algorithm 256 (SHA-256) and the RACE Integrity Primitives Evaluation Message Digest 160 (RIPEMD-160).
Beginning with the public key, this string of values is first ran through the SHA-256 hashing algorithm to produce a hash, and then that hash is computed using RIPEMD160 to produce a bitcoin address. The bitcoin address, and addresses in other cryptocurrency systems, are what often appears in a transaction between two parties, with the address signifying the recipient of the funds.
Private Keys
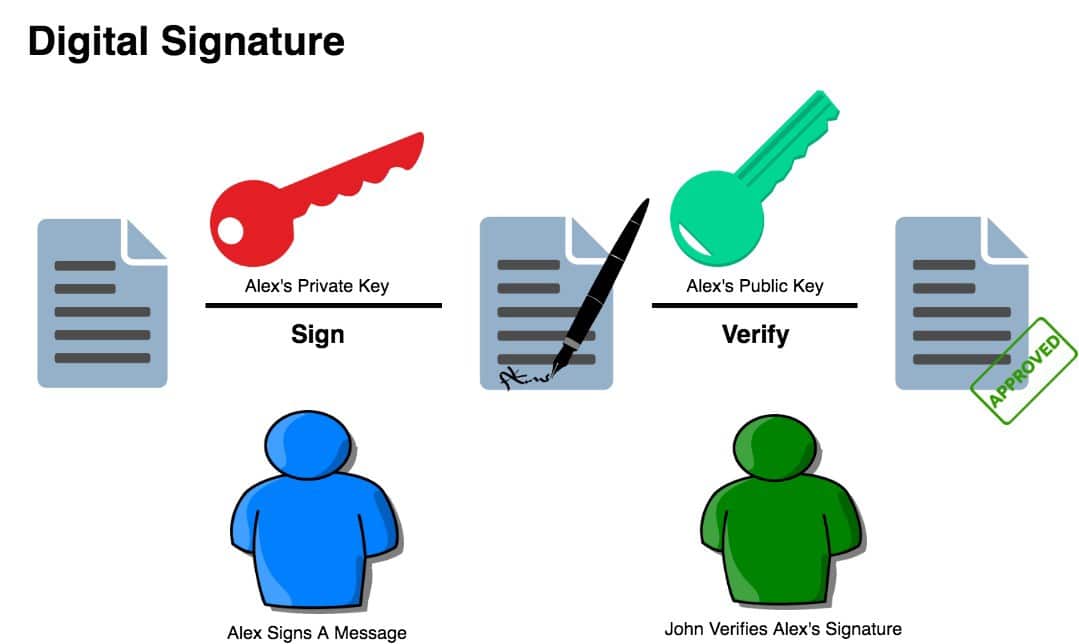
The private key consists of alphanumerical characters that give a user access and control over their funds to their corresponding cryptocurrency address. The private key is used to sign transactions that allow the user to spend their funds. In other words, the private key creates unique digital signatures for every transaction that enable a user to spend their funds, by proving that the user does in fact have ownership of those funds.
For example:
When Bob decides to buy a coffee from Alice's store using 5 bitcoins, he provides his public key and a digital signature generated by applying his private key to the transaction. The digital signature is a unique cryptographic proof that can only be generated by someone with knowledge of the private key, which is Bob in this case.
However, anyone with access to the public key and digital signature can use these elements to verify that Bob is the legitimate owner of the 5 bitcoins. This verification process allows all other participants on the Bitcoin network to validate and accept Bob's transaction as authentic without requiring Bob's private key to be disclosed.
Digital Signatures
A digital signature is a mathematical scheme that is used for showing the authenticity of a digital message or document. A digital signature that is valid will give the recipient of a digital message or document reason to believe that the message or document was in fact created by a known sender. A digital signature also indicates that the sender cannot in any way deny having sent the message or document, and that the message or document was not altered at any point while it was in transit.
Digital signatures play an important role in cryptocurrency systems, because they prove ownership of funds and allow the individual in control of those funds to spend them.
For example, the digital signature algorithm that is utilized in Bitcoin is known as the Elliptic Curve Digital Signature Algorithm, which is also known as ECDSA. ECDSA is the algorithm that underpins the signature scheme in Bitcoin, and it is based on elliptic curve cryptography. This is the same cryptographic approach that is used in producing private and public key pairs. In Bitcoin, a digital signature is effectively intended to serve three distinct purposes:
- Firstly, a digital signature serves as proof that the owner of a private key, who will by extension have ownership of his/her funds, has indeed authorized that those funds can be spent.
- Secondly, a digital signature serves as proof that the authorization is undeniable.
- Thirdly, a digital signature proves that the transaction that has been authorized by the signature has not or cannot be modified by anyone after it has been signed.
Digital Signatures in Bitcoin: How They Work
As mentioned before, a digital signature is a mathematical scheme, and this mathematical scheme consists of two parts. The first part is an algorithm that creates the signature. This signature is created using a private key (which is also known as the signing key) and the hash of the transaction that is to be signed. The second part of the mathematical scheme is an algorithm that allows anyone to verify that the digital signature that is produced is valid.
The first part of producing a digital signature in Bitcoin can be represented mathematically in the following way:
Sig = Fsig(Fhash(m),dA)
Where:
- dA is the signing private key
- m is the transaction
- Fhash is the hashing function
- Fsig is the signing algorithm
- Sig is the resulting signature
The signing function (Fsig) produces a signature (Sig) that comprises of two values: R and S:
- Sig = (R, S)
Once R and S have been calculated, they are serialized into a byte stream that is encoded using an international standard encoding scheme that is known as the Distinguished Encoding Rules (or DER). In order to verify that the signature is valid, a signature verification algorithm is used. Verification of a digital signature requires the following:
- Signature (R and S)
- Transaction hash
- The public key that corresponds to the private key that was used to create the signature
Verification of a signature ensures that only the individual possessing the private key, which generated the corresponding public key, could have produced the signature for the transaction. When the signature is subjected to the verification algorithm, it will yield a result of ‘TRUE' if the signature is deemed valid. This process confirms the authenticity and integrity of the signature, providing assurance that it was indeed produced by the rightful owner of the private key.
Conclusion
Understanding the concepts of public keys, private keys, cryptocurrency addresses, and digital signatures is crucial in comprehending the underlying mechanisms of cryptocurrency systems. Cryptography plays a fundamental role in securing data and enabling ownership features within these decentralized networks.
Public keys and private keys form a key pair that ensures secure transactions and ownership verification. Cryptocurrency addresses, derived from public keys, serve as unique identifiers for user accounts. Private keys, kept confidential by users, authorize transactions and generate digital signatures that prove ownership and integrity. Verification algorithms validate the signatures, ensuring that only the rightful private key owner can produce valid signatures. These cryptographic elements collectively establish the foundations of trust and security in the world of cryptocurrencies.





[…] debated is whether the same conclusion applies in relation to public keys. A public key is cryptographically connected to a cryptocurrency address in the sense that the address is a […]
Comments are closed.